In the SAP Easy Access menu choose Tools Administration User Maintenance Information System Roles Roles By Complex Selection Criteria and then Execute. Role s Change Sales Order SAP Transaction s VA01.
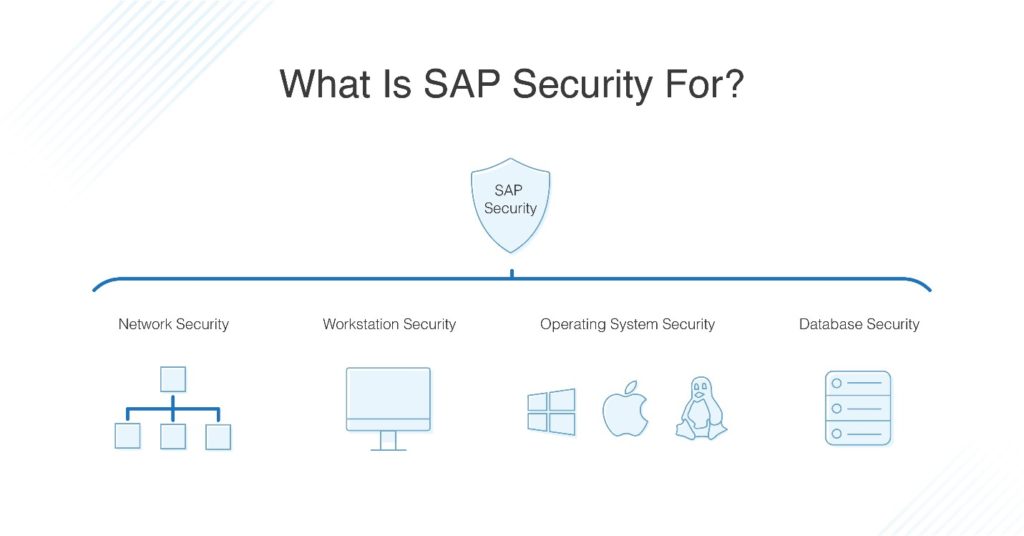
Sap Security Tutorial For Beginners Dnsstuff
The BPPs are used for building training and integration testing scenarios.
. The Security Matrix helps to view the roles in an easy-to-read format and helps the SAP Security Team communicate to the functional teams the security roles being configured. A Practical Guide to SAP Audithttpsamznto2O1cDK6Security Audit and Control Features SAP ERP 4th EditioNhttpsamznto2K3UUR8. In a SAP system human errors negligence.
Tasks include SAP Security Role Design coaching less experienced SAP Analysts in the US. The transaction and valuecontroller role concept deals with the design of individual transaction roles and authorization objects. However one important goal of an organization in its security design is to minimize the number of roles in the system.
SAP System Security in Unix and Windows Platform Single Sign-On Concept So the security in SAP system is required in a distributed environment and you need to be sure that your data and processes support your business needs without allowing unauthorized access to critical information. Transaction in Role Menu Authorization Data and so on and for each option there is a different Lay-out report. Surviving an SAP Audit.
The approach of creating master also referred as Template roles and then derive the master roles into children roles with different organization attributes can meet the requirements. In role administration Tools Administration User Maintenance Roles choose the input help for the Role field. Proficient with SAP authorization concept role design user administration SOD conflict resolution.
This guides explains the new role development framework for SAP HANA using XS Advanced and HDI. The design-time definition of a role is specified in a text file with the extension hdbrole. Implementing a strong Security strategy with policy adherence is requisite to manage compliance minimize risks and to setup a secure and efficient authorization concept with process efficiency and adoption which can be based on organizational structures.
It gives recommendations and provides examples on how to best build roles. Business processes and Role based Authorization Concept. The client to design and implement a new SAP security design following our tier 4 methodology.
At current cleint I tried to sell this idea and tried to avoid composite role design because of problems I have seen after go-live SODs maintainence issues problem analysis. Strong knowledge in SAP Security tables and ability to efficiently and accurately identify authorization errors using SUIM SU53 and ST01 to provide consultative support to business. Role-based permission is essential for the good security design of SAP SuccessFactors Onboarding solution.
Transaction Value Roles. Provide audit services to detect deviations of established procedures role mappings as well as unauthorized. Can somebody please provide the Role to T-Code matrix or any document to facilitate the role design workshops with BI Functional Teams which are starting next week.
Checkout Our Frequently Asked SAP Security Interview Questions. A good security design ensures that an organization can manage the proper authorization data privacy data integrity etc. You use the role editor of the SAP HANA studio to create a role in the SAP HANA repository.
Contents 9 12 SAP NetWeaver Business Intelligence 245 121 Introduction and Functions. Best practices and examples for developing roles in SAP HANALearn about building HDI containers and their setup create design-tiem objects in MDC and about granular roles adminstration roles security roles and support roles Download the Document. SAP Security Architect will complete application security tasks covering all aspects of audit design testing and implementation of SAP roles through project work incidents and service requests.
In this module special care must be given to roles since the target population is external users of the system. The activated role is now visible in the Systems view under Security Roles following the naming convention. SAP Tables for Role Changes information.
Security and Role Design Service The regulatory and compliance landscape of today requires companies to ensure critical business applications such as SAP are properly secured and adhere to stringent guidelines related to privacy proper segregation of duties and limiting access to sensitive business and system transactions in order to prevent financial misstatements or. Security Design Approach Observation 3 SAP Position Customer Service SAP transaction s are assigned to roles but a transaction should only be assigned to one role. The implementation of the new SAP security design helped this client reduce the number of roles in the SAP environment which combined with the SAP GRC Access Controls application facilitated the overall user provisioning processes.
You must define security roles. Role Design Startegy. Minimum 5 years experience in GRC 10.
Best practices and recommendations for developing roles in SAP HANA. 5 years of working experience with SAP system security including but not limited to access controls process controls role design and maintenance. Roles are mapped to SAP positions which are then mapped to users.
When I enter through SUIM -- Change Documents -- for Roles T-code RSSCD100_PFCG I can see that there are few options to choose which kind of changes you would like to see for exm. The functional teams can use the security matrix to assist in adding theroles to their BPPs business process procedures. Security and Role Design Service.
The transactional role also handles the authorization objects. I am strong believer that SAP Security role design startegy should be simple and easy to manage with single roles rather than having composites. Authorization objects deal with the final transaction access.
SAP Provisioning can be handled in different ways. Best practices and examples for developing roles in SAP HANA. Design test troubleshoot and maintain security roles across the SAP platform working closely with business users functional teams and technical teams to ensure that appropriate access controls are integrated within the roles.
5 years of specific SAP GRC Access Control working experience including but not limited to access request management access risk analysis emergency access management and business role management.

Sap Implementations In Public Sector Implemantation Of Sap Security For A Public Sector Organization Part I

Sap Security Role Design Best Practice Youtube

Best Practice Sap Role Re Design Youtube

Identity Management And Sap Users Roles And Transactions Part1 Ibm Security Identity And Access

2015 Sap Hana Security Documentation Sap Hana Roles Explained I Youtube



0 comments
Post a Comment